Apple is reportedly ditching Intel for 5G chips in the iPhone
The likes of Intel and Qualcomm may well be locked in a battle over next-gen communications chips, which will help phones connect to futuristic 5G networks in the future. And the biggest of those contracts, at least when it comes to consumer devices, has to be the iPhone. We can now rule out one major player in the race to supply the world with 5G chips — Apple has reportedly notified Intel that it will not be using its modems for 2020 iPhone models. The news was first reported by Calcalist.
The fact that Apple has notified Intel that it won’t be using its chips may have wide implications for Intel. As a result of the decision, Intel has reportedly halted development on a modem internally known as “Sunny Peak,” and the team working on the modem redirected to other Intel efforts. Reports note that Intel expected Apple to be the main customer for these new modems.
All hope may not be lost for Intel. The company is reportedly now focusing on improving its product in an attempt to win Apple back for the 2022 iPhone lineup.
The news isn’t completely surprising. In June, Bloomberg reported that Apple was looking to move away from Intel chips, instead turning to MediaTek for its communications components. On top of that, there have been plenty of reports indicating that Apple was looking to move away from using Intel processors altogether by 2020 — which lines up with this new report.
Of course, until 2020, Intel’s modem business may be better than ever. Apple has also been trying to reduce its dependence on Qualcomm chips, and because of that has moved to using Intel components in modern iPhones. That is likely because of the ongoing legal troubles between the two companies, which are expected to last for some time.
It will be interesting to see what Apple does do come 2020. While it may completely turn to MediaTek for internal components, it may also improve its relationship with Qualcomm, or perhaps it’s hoping to instead use its own tech, which would help give it more control over the iPhone and how much an iPhone costs to make.
Editors’ Recommendations
- AT&T brings ‘5G Evolution’ to more than 100 new markets
- Apple vs. Qualcomm: Everything you need to know
- Is Apple poaching Intel talent from a new hush-hush facility in Oregon?
- Apple iPhone X Plus: News, rumors, specs, and more
Cryptocurrency may be why you still don’t have Nvidia GTX 11 Series graphics
Unnamed sources in the supply chain point to the current overabundance of add-in desktop graphics cards as to why you’re not already seeing Nvidia’s new GeForce GTX 11 Series on store shelves. Nvidia reportedly has around 1 million chips ready for release but is holding back because there is simply no room for the next-generation cards. This is why Nvidia CEO Jensen Huang said in June that the launch would be “a long time from now.”
The problem stems from cryptocurrency. Throughout 2017, as values climbed through the roof, miners scooped up every graphics card they could find, leaving store shelves barren. The few cards you could find on the internet suffered crazy overinflated prices due to sellers taking advantage of the product void. To meet the rising demand in the cryptocurrency and gaming markets, Nvidia and its partners created more cards.
But then in 2018 cryptocurrency prices tanked. Individuals and small organizations closed shop while the larger miners cut back on their purchases including the ASIC systems designed specifically for cryptocurrency mining. With all that digital coin digging slowing to a crawl, the market currently has“around several million units” collecting dust on store shelves.
To make room for new GTX 11 Series products, graphics card prices may be reduced 20 percent starting in July. Prices presented by retailers may get even lower once cryptocurrency miners begin selling their used equipment at dirt-cheap prices. The current overflow likely affects the revenue of every party involved including Nvidia, its partners, the company that actually manufactures the chips (TSMC) and more.
China’s Sichuan province could help with the overstocking issue. This region accounts for nearly 70 percent of China’s mining operations, which recently faced severe flooding that damaged many of its cryptocurrency mining operations. These operators will be looking to replace their damaged hardware including whatever Nvidia-based graphics cards they had installed.
Despite the inventory issue, Nvidia’s GTX 11 Series may still get an introduction during Gamescom in August. Nvidia is sending individuals in the press out to the convention in Germany, meaning the company likely isn’t spending that kind of money just to showcase PC games running on current hardware. There is no reason why Nvidia couldn’t reveal the series at that time if the company has the hardware ready. But a retail release could reside in the fourth quarter, depending on the current-generation stockpile.
Most of the “Turning” GPUs Nvidia reportedly has locked and loaded will ship out to third-party manufacturers while the company will reserve a batch for its own first-party “Founders Edition” cards. Previous reports said Nvidia’s partners would receive the chips by the end of August or early September, putting product availability between weeks or several months thereafter. Mass production of Micron’s GDDR6 graphics memory didn’t even begin until June.
The GTX 11 Series will include both desktop and mobile products later this year, including the GTX 1180 add-in card and the GTX 1160 6GB chip for notebooks.
Editors’ Recommendations
- Nvidia may release the GTX 1180 Founders Edition in July
- Nvidia saw a revenue spike from sales of graphics cards to crypto miners
- Nvidia could debut GTX 11 Series graphics cards during Gamescom
- Nvidia graphics cards may be back in stock, but they’re disappearing quick
- Nvidia’s GTX 11 Series may get people ready for the next generation of VR
Cheap Android phones are selling user data in developing countries
Data is collected and sold through the guise of a firmware update app.
User data and the privacy surrounding it has been a particularly hot topic this year, and while there’s been plenty of talk regarding it in the U.S., a new light is being shown onto this matter in developing countries.

According to a report from The Wall Street Journal, an Android phone called the Singtech P10 that’s sold in Myanmar and Cambodia actively collects various bits of information from users of the phone and sells it to an advertising company called General Mobile Corp. (aka GMobi) in Taiwan.
Per The Wall Street Journal:
Taipei-based GMobi, with a subsidiary in Shanghai, says it uses the data to show targeted ads on the devices. It also sometimes shares the data with device makers to help them learn more about their customers.
As for what kind of data is being shared, it’s reported that the GMobi app gathers IMEI numbers, MAC addresses, and even location data that’s then sent off to GMobi servers over in Singapore.
Per Mark Groman, former Senior Privacy Adviser at the White House Office of Management and Budget:
They are exploiting developing economies and individuals who can’t afford better devices and clearly tracking them.
As WSJ continues:
Many popular smartphone apps collect user data such as contacts and even locations, but users typically install such apps, actively consent to the data collection and can delete the apps at any time. GMobi’s software comes pre-installed on new smartphones out of the box, and it can only be removed by taking elaborate technical steps.
GMobi’s website lists that it works with Huawei, Xiaomi, and BLU, but all three companies told The Wall Street Journal that they have never worked with the company (BLU did have a relationship with GMobi competitor Adups but has since terminated it).
There are certainly improvements we can make in the U.S. and other developed parts of the world when it comes to the way data is handled, but at the very least, we don’t have to deal with this sort of madness on a daily basis.
Best Cheap Android Phones in 2018
How to Access Controls for USB Restricted Mode in iOS 12
iOS 12 includes a new feature called USB Restricted Mode, which is designed to make your iPhone and iPad immune to certain hacking techniques used by law enforcement and other potentially malicious entities to gain access to an iOS device.
There are some iPhone access methods that use a USB connection, downloading data from your iPhone (or iPad) through the Lightning connector to crack the passcode.
iOS 12 prevents this by disabling data access to the Lightning port if it’s been more than an hour since your iOS device was last unlocked.
This feature is enabled by default, but there are some situations where you might want to turn it off, such as when using CarPlay to drive long distances when you might not be able to unlock your iPhone for a few hours. Here’s how to access the setting:
Open the Settings app.
Choose Touch ID & Passcode or Face ID & Passcode, depending on the device.
Enter your passcode to access the settings. 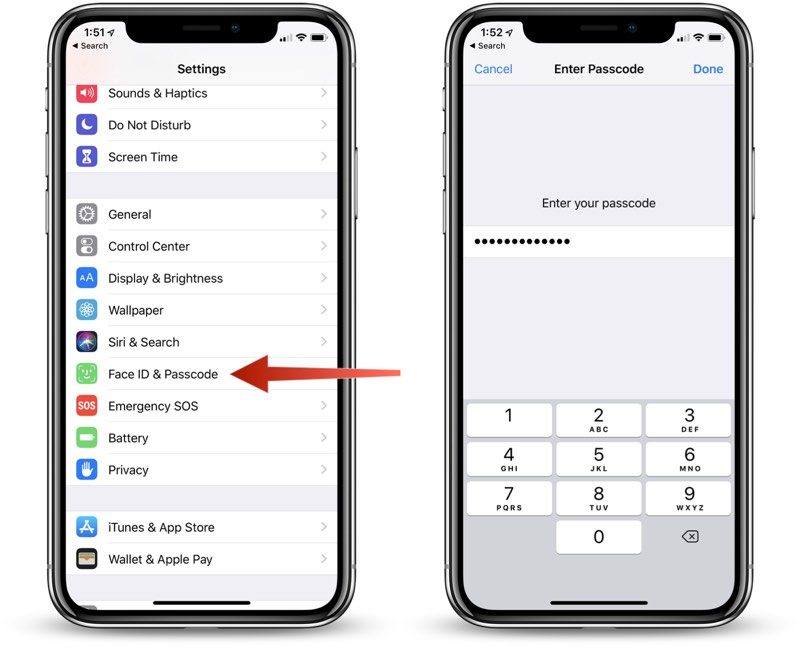
Scroll down to the bottom of the app where it says “USB Accessories.”
Leave it toggled off to disable access to your iOS device if you want it to refuse USB connections if it’s been more than an hour since the iPhone or iPad was unlocked.
Toggle it on if you want USB accessories to be able to connect even if it’s been more than an hour since the iPhone or iPad was unlocked. 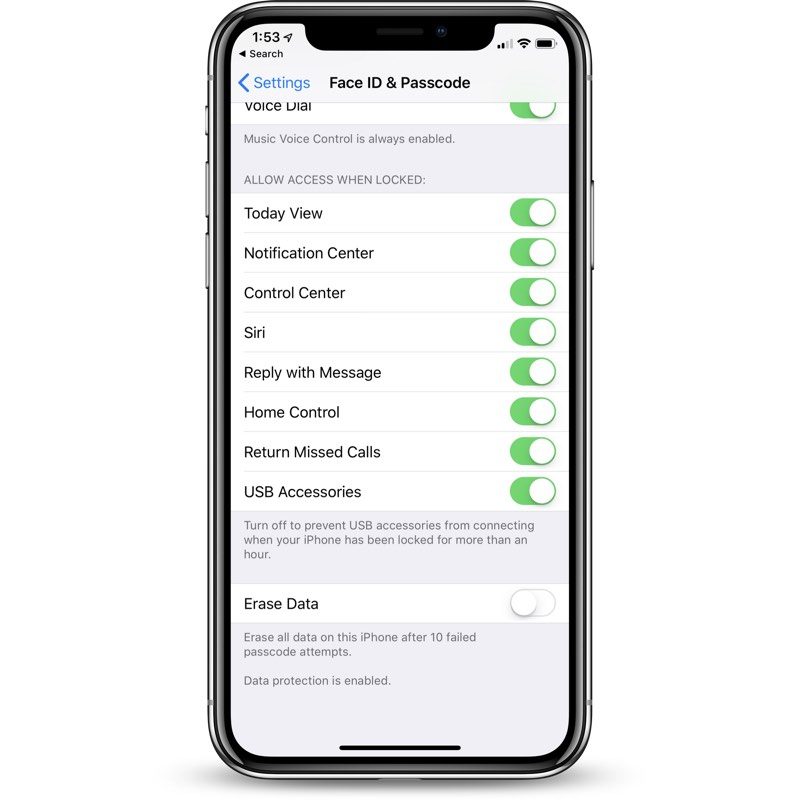 Most people are going to want to leave this toggle in its default off position for extra protection.
Most people are going to want to leave this toggle in its default off position for extra protection.
In normal usage, most of us unlock our iPhones every hour or two, and if you do need to plug your iPhone or iPad into a computer to access it, you can just enter your passcode to allow data access if it’s been over an hour since the iPhone was last unlocked.
Right now, in the iOS 12 beta, these USB restrictions do appear to shut down access to a wired CarPlay interface after an hour, so that’s one exception where people might want to turn this setting on to disable the restrictions on the USB port. From the iOS 12 beta notes:
“If you use iPod Accessory Protocol (iAP) USB accessories over the Lightning connector (such as CarPlay, assistive devices, charging accessories, or storage carts) or you connect to a Mac or PC you might need to unlock your device to recognize the accessory.”
Note: Even if data access to USB port has been disabled because it’s been over an hour since an iPhone was last unlocked, it continues to be able to charge through a standard Lightning cable because the power connection is not disabled.
Related Roundup: iOS 12
Discuss this article in our forums
Tesla Powerwalls keep Vermonters comfortable and safe during heat wave
As the summer heat wave drags on, nearly 500 Vermont homes with Tesla Powerwall batteries are staying cool, reports VermontBiz. The state’s Green Mountain Power (GMP) electric company stored-solar-power project is paying off for the utility company and its customers.
GMP launched the Powerwall program in 2015. The goal is to install the energy storage devices in 2,000 homes, according to Electrek. Residential Powerwall installations started slowly, with approximately 220 installed by April, GMP told Electrek at the time. GMP also noted in April that the demand for Powerwalls was building, with 1,200 homeowners interested in the heavily subsidized units.
Additional home energy storage examples
Tesla home battery packs in Canada
Tesla home Powerwalls sell out quickly
Tesla announced Home Powerwall energy storage
Normally it costs about $7,000 for a residential Powerwall installation. GMP subsidizes the program with two options. Customers can pay $15 a month or a $1,500 one-time charge. The huge discounts work for GMP, however. Part of the deal is that customers allow GMP to treat the Powerwall units as “virtual power plants” to access stored energy for the grid.
The current installed base also means GMP has potential 5,000 kWh of stored energy to access during periods of peak demand.
The residential Powerwalls are charged by homeowners’ on solar panel arrays or by conventional power loaded when demand is low. According to Green Mountain Power, the utilities conventional power sources are 90 percent carbon-free — so any argument that the company burns dirty fuel to charge the batteries is not valid.
GMP’s “green power” sources include solar farms, wind power, hydroelectric plants, and cow manure. The Cow Power program currently consists of 14 farms with approximately 13,500 cows. By burning the methane waste from cows, GMP cuts carbon emissions and produces power. The program powers 3,200 Vermont homes with the equivalent of 8.2 million gallons of gasoline by burning 73,000 tons of methane each year.
With almost 500 Powerwalls in Vermont homes, the comfort and safety factors of backup power during the prolonged summer heat, it’s a good bet GMP customers will sign up for the remaining units.
“We know our customers are environmentally conscious and make smart choices about their energy use every day. In this heat wave, our customers’ safety and comfort is key. We are so glad to be able to leverage innovation like battery storage to bring down costs for customers and keep them comfortable and safe,” Josh Castonguay, vice president and chief innovation officer at GMP, said in a statement. “Our growing network of stored energy is allowing us to use technology, in partnership with our customers, to deliver innovative solutions today.”
Editors’ Recommendations
- Samsung has made a very big promise for 2020, and it’s not for the Galaxy S12
- California prepares to lead the nation in solar-equipped housing
- World’s largest battery on a desert solar farm would triple Tesla’s record
- Google Assistant grows hookup list to over 5K smart home devices, appliances
- PG&E applies to build Tesla’s largest battery farm yet in Silicon Valley
A.I. players master ‘Quake III Arena,’ manage to outperform humans
Those among us who fear that we’ve already passed the point of no return when it comes to artificial intelligence becoming self-aware and plotting to murder the human race will likely cite A.I. research company DeepMind’s latest experiment as further proof of that notion. Using Id Software’s Quake III Arena, DeepMind has managed to train artificial players to be even more effective than their human counterparts.
The challenge for DeepMind was not to see if its A.I. agents could defeat human players in battle, but rather if they could work together on procedurally generated levels to complete an objective — in this case, capture the flag.
Because the levels’ structure changes each time they play, the agents are unable to simply memorize locations in order to make it to the flag. This forced them to actually learn the strategies needed to win in a similar manner to how human players might improve at the game. The agents even used an emulated game controller to control their characters in Quake III Arena.
“The agents are never told anything about the rules of the game, yet learn about fundamental game concepts and effectively develop an intuition for capture the flag,” DeepMind said in a blog post. “In fact, we can find particular neurons that code directly for some of the most important game states, such as a neuron that activates when the agent’s flag is taken, or a neuron that activates when an agent’s team is holding the flag.”
As the A.I. agents won matches, the behavior they used to do so was reinforced and these agents were paired up with human players to impressive results. Eventually, DeepMind held a Quake III Arena tournament, and not only did these A.I. agents have a higher success rate than humans, they were also rated as “more collaborative” in a post-tournament survey. Unfortunately, just like with so many children on Xbox Live, the A.I. agents also learned to “camp.” Maybe it is a legitimate strategy.
You can watch a full deep-dive video on the Quake III Arena project above. Visual settings have been greatly reduced, as the A.I. don’t actually care how their game looks.
Editors’ Recommendations
- Can’t get enough of ‘Doom’? A.I. can generate an infinite number of new levels
- Machine learning? Neural networks? Here’s your guide to the many flavors of A.I.
- Microsoft wants artificial intelligence to catch cheaters on Xbox Live
- What is an artificial neural network? Here’s everything you need to know
- This chessboard isn’t haunted, it just moves the pieces on its own
How to use BlackBerry’s Privacy Shade
Andy Boxall/DigitalTrends.com
Whether you think it’s important or not, there has been more attention drawn to online privacy recently than ever before. But what about keeping activity on your phone private? We’re talking about the prying eyes of the guy sitting next to you on the train, or another with a long-lens camera sneaking on your emails. The most secure password in the world can’t stop that.
What you need is BlackBerry’s Privacy Shade, a feature that comes pre-installed on its BlackBerry KeyOne and BlackBerry KeyTwo Android smartphones, and is also available as a stand-alone app for other Android phones.
Here’s how to find Privacy Shade on your BlackBerry, or use it on a different Android phone.
Find Privacy Shade on the BlackBerry KeyOne, and Key2
Andy Boxall/DigitalTrends.com
Privacy Shade is found in the Android Notification Shade. Drop it down with a swipe to expose all the shortcuts at the top of the screen. If it’s not there, hit the Edit button that looks like a pencil and see if the Privacy Shade tile is waiting there. If so, tap and drag it into the shade.
If you still can’t see it, you may have to activate the feature from the app. Either using the Google search bar on the home screen or the search bar in the app menu, find Privacy Shade and follow the on-screen instructions to set it up.
How to use Privacy Shade on the BlackBerry KeyOne, and Key2
Andy Boxall/DigitalTrends.com
Tap the Privacy Shade icon in the notification shade. A bar will appear over the screen, obscuring everything around it and leaving only the section it hovers over visible. This means only that area can be viewed, keeping surrounding information completely hidden.
It’s best suited to reading emails, Facebook, Twitter, or other written content, as navigating the phone is a chore like this. Tap and hold the Eye icon under the shade to move the exposed area up and down the screen. Double tap the Eye icon to increase the size of the window, or to shrink it down again.
Andy Boxall/DigitalTrends.com
At the top right of the screen are two buttons. The square with the arrow inside exits Privacy Shade, while the three dots opens a menu to customize the Shade. Five different options appear when you tap this menu. The first, which is a rectangle, changes the shade to a circular view, or turns off the shade entirely, for a blank screen.
Andy Boxall/DigitalTrends.com
The button below, a circle with a line through it, is like a light switch. Tap it and the shade will darken until you tap and hold the Eye icon. Remove your finger, and it darkens again. Under this is a button to change the size of the Shade area, and the button shaped like a water droplet is for changing the opacity of the screen around the Shade. This goes from completely black, like the screen is off, to still slightly visible.
Privacy Shade on other Android phones
Andy Boxall/DigitalTrends.com
BlackBerry offers the Privacy Shade as a stand-alone app from Google Play for other Android phones. When you open it for the first time it will prompt you to also install the BlackBerry Hub+ app. This is also used by other BlackBerry apps including BlackBerry Calendar and various third-party apps, as a general notification platform.
Andy Boxall/DigitalTrends.com
However, if you only want to use Privacy Shade, you don’t have to add any other services or grant the extensive permissions that the Hub+ demands. Privacy Shade on any other Android phone operates in exactly the same way as it does on the KeyOne or Key2, and all the instructions above apply. We used the app on the OnePlus 6, and it worked faultlessly.
There is one major difference between the Google Play app and the version on a BlackBerry phone. Privacy Shade is a BlackBerry feature and therefore free on its own Android phones; but because it’s part of BlackBerry Hub+ for other phones, a $1 monthly subscription charge is applicable. You can try Privacy Shade for 30 days without charge to see if it’s worth the money.
Now you can browse the web and read those secret emails in peace, almost anywhere, without worrying about your privacy.
Editors’ Recommendations
- Blackberry Key2 tips and tricks
- BlackBerry Key2 vs. BlackBerry KeyOne: A stunning successor
- BlackBerry Key2 review
- BlackBerry Key2 vs. OnePlus 6: Which fan-favorite will win?
- Blackberry Key2 vs. Samsung Galaxy S9 and S9 Plus: Is it a contender?
Outlook.com to get Dark Mode for reading email at night
The Outlook.com feedback hub reveals that a dark mode is coming to Microsoft’s online email client. The company revealed a sneak peek in October 2017, but a representative says it was merely a prototype that needed lots of work to be worthy of mainstream use, hence current the delay. The final ready-to-use version should appear on Outlook.com “soon.”
“One reason for the delay is our insistence that we deliver the best Dark Mode of any leading email client (you’ll understand when you see it, I guarantee),” the representative says in a post response. “We’ve redesigned the colors and code multiple times and are proud to enter the final stretch.”
The news arrives by way of a post on Microsoft’s Outlook.com forum where one user said a dark/night mode is essential and “a necessary feature.” So far, the post received 1,013 votes and falls behind other complaints including problems with the new layout (1,038 votes), an issue with automatically opening emails (1,065 votes), the difficulty in distinguishing read and unread messages (2,623 votes), and more.
Currently you can change themes on Outlook.com, but that simply alters the colors of the toolbar, category highlight bar, and a few text headers. Overall the web client is a brilliant white, which could be somewhat blinding if you’re working in a low-light environment. That’s where a dark mode would come in handy as seen in Windows 10. Unfortunately, changing your browser’s theme won’t change the overall look of Outlook.com.
“Like you, we eagerly await the day this is finally available to the public. I am elated to announce that that day is very soon,” the representative adds.
Although Outlook.com is free to use for anyone with a Microsoft account, the company introduced “premium” features for Office 365 subscribers in October 2017. The benefits include an ad-free experience, real-time link checking to prevent malware, real-time attachment scanning, 50GB of storage, and premium support provided by the Outlook team.
Microsoft updated the back end of Outlook.com in October 2017 to determine your physical location and move your data to the nearest datacenter. That doesn’t mean Microsoft will move your data if you’re a Virginian on vacation in Paris, France. Instead, if you move to Paris, your data will eventually shift over to the closest data center as well.
Editors’ Recommendations
- Get your pickaxe ready: The next MineCon Earth show streams in September
- Windows 10’s Mail app may display an Office 365 ad for some users
- You’ll never read Facebook’s new data policy, so we did it for you
- Google wants to let you vote from your Android phone
- MacOS Mojave brings Dark Mode, stacking, and a redesigned App Store to Macs
Your body heat can help attackers steal your password in new attack
If you’re typing your password on a computer keyboard, you’re leaving heat traces behind that could be picked up by hackers. By using a thermal imaging camera and scanning your computer keyboard after you typed your password, researchers at the University of California, Irvine discovered that key presses can be recovered as late as 30 seconds after the first key was pressed with off-the-shelf solutions from FLIR. The researchers published their findings on attacks by thermal imaging in a paper titled “Thermanator.”
“Although thermal residue dissipates over time, there is always a certain time window during which thermal energy readings can be harvested from input devices to recover recently entered, and potentially sensitive, information,” the researchers wrote.
This style of attack was tested on four keyboards, and researchers found that a full password can be obtained by scanning thermal residues on keyboards within 30 seconds of the first key being entered. And after one minute, partial passwords can be obtained from the thermal scans. For their experiment, researchers set the infrared heat-detecting FLIR cameras on a tripod 24 inches away from the keyboard.
FLIR makes several models of its infrared cameras that capture heat. The basic model, called the FLIR One Pro, is a $400 accessory that is available as a smartphone attachment. Some phones, like the CAT S61, also ships with the FLIR camera module embedded.
Thirty non-expert users tried to guess the password based on the infrared thermal imaging scans. When “hunt and peck” typists entered their passwords, researchers found that the participants were able to guess secure passwords between 19.5 and 31 seconds after initial entry by examining the infrared thermal scans. Weak passwords, such as “football” and “12341234” can be obtained an average of 25.5 seconds and 45.25 seconds, respectively. Conversely, for touch typists, the “12341234” password was deemed the best of the tested combination in the study, requiring non-experts 47.6 seconds on average to guess, TechRepublic reported.
UC Irvine researchers concluded that hunt and peck typists were the most susceptible to Thermantor-style. By using just their forefingers to type, they leave a larger fingerprint on each key, leaving behind more heat trace. Because touch typists rest their fingers on the row of home key on a keyboard, they generate more thermal noise, making it difficult to analyze heat traces using the FLIR camera. However, those with acrylic fingernails are more immune to Thermanator attacks, because they type with the tip of their fingernails, leaving no heat traces behind on the keycaps.
“The main takeaway of this work is three-fold: (1) using external keyboards to enter (already much-maligned) passwords is even less secure than previously recognized, (2) post factum (planned or impromptu) thermal imaging attacks are realistic, and finally (3) perhaps it is time to either stop using keyboards for password entry, or abandon passwords altogether,” researchers said.
Additionally, if you have to enter your password in a public environment, one method to keep your information secure is to use two-factor authentication.
Editors’ Recommendations
- Ransomware shifts focus from holding passwords hostage to hijacking your PC
- How to change your Gmail password
- Amazon Key program expands to put your junk in your trunk
- The sound of destruction: Malicious video, audio files could attack laptops
- An all-in-one botnet is on the rise, packing a scary buffet of attacks
Apple registers 10 unannounced MacBook and iPad devices overseas
French website Consomac discovered that Apple registered unannounced MacBooks and iPads with the Eurasian Economic Commission. The filings are a requirement for encrypted devices that will be sold in Armenia, Belarus, Kazakhstan, Kyrgyzstan and Russia. Apple listed five MacBook models and five iPad models.
For starters, the five MacBook products list as A1931, A1932, A1988, A1989 and A1990 with MacOS 10.13 as the operating system. The last three numbers may consist of a new 13-inch MacBook Pro (A1988), a 13-inch MacBook Pro with Touch Bar (A1989), and a 15-inch MacBook Pro with Touch Bar (A1990). The first two may refer to a refreshed 12-inch MacBook (A1931) and a MacBook Air replacement (A1932).
Unnamed sources said earlier this year that Apple would introduce an entry-level 13-inch MacBook in the second half of 2018, killing off the “Air” brand. Right now, the 13-inch MacBook Pro without the Touch Bar serves as an alternative to the MacBook Air, but the Pro device has a starting price that’s $300 more than the current lightweight Air. Even the 12-inch MacBook can’t match the MacBook Air’s $999 starting price.
But Apple analyst Ming-Chi Kuo of TF International indicated otherwise in June. He expects the entry-level 13-inch MacBook to keep the “Air” brand and sell for an even cheaper starting price than the current $999 model. The series launched in 2008 with a single 13-inch model and experienced yearly hardware updates until 2015. Apple added an 11-inch model in 2011 until 2015 as well. Apple refreshed the 13-inch version in 2017, leading to speculation that perhaps the “Air” family was coming to a close.
As for the five iPad models, they consist of the A1876, A1934, A1979, A2013, and A2014. The models aren’t quite as easy to determine in this case although a guess would put the A1876 as the iPad Mini 5, the A1934 serving as the “vanilla” iPad, the A1979 for the 10.5-inch iPad Pro, and possibly two 12.9-inch iPad Pro variants. All five are listed with the iOS 11 operating system.
Reports surfaced at the end of 2017 that the iPad Pro models launching by the end of 2018 would incorporate a few designs pulled from the iPhone X. For instance, Apple will supposedly remove the Home button and extend the screen out to the edges in every direction. They will also supposedly support Face ID for unlocking the device, logging into apps, and making payments.
Why Apple lists iOS 11 and MacOS 10.13 with its upcoming devices is unknown, but the company may be required to list a non-beta compatible platform that’s part of the encryption process. MacOS 10.14 and iOS 12 are currently in beta and slated for a release later this year. Apple may wait until both the new software and new hardware are complete to better highlight their union during the expected official reveal slated for the end of 2018.
Editors’ Recommendations
- A new MacBook Air likely won’t be revealed until later in 2018
- The latest version of MacOS now supports storing your messages in Apple’s cloud
- MacBook Pro 13-inch with Touch Bar review
- A cheaper MacBook Air could still arrive in late 2018
- Apple Store hints you shouldn’t buy a new MacBook Pro until after WWDC




